Lecture 33
IP Next generation, IPv6, IP Next Layer (IPNL)
By
Santosh Kumar(Y0301)
In
this lecture two extensions of IPv4 will be disscussed which are as
follows:
- IP Next Generation or IPv6
- IP Next Layer
IPv4 Address Exhaustion
Problems
A network can have a private network address space, as long as, it does not want to link itself to the Internet. In order to link to the Internet, every network needs a globally unique IP address. Due to exponential increase in the number of users of Internet and increase in number of networks linked to the Internet, the IP addresses are running out fast. This is due to a fixed structure of IPv4 headers which allows and supports only 32 bit addresses. Besides, there are some other problems associated with IPv4 addressing schemes. One of the problems is the coarseness of granularity of address allocation schemes. IPv4 supports four classes which are as follow:
CLASS
|
#of Networks
|
#of Hosts
|
A
|
126
|
16,777,214 |
B
|
16382
|
65534
|
C
|
about 2 mill. nets
|
254
|
D
|
multicast network class
|
|
There were two fast fixes applied to solve this problem which we
discuss below.
Solutions
Classless Inter-Domain Routing
allows for more efficient allocation of IP addresses than IPv4. Here,
the addresses are independent of classes. In CIDR, network identifier or
prefixes can be anywhere between 13 to 27 bits. This provides a much
finer granularity of address space allocation which better fits the
needs of any organizations. A CIDR address includes the standard 32-bit
IP address and also information on how many bits are used for the
network prefix. For example, in the CIDR address 206.13.01.48/25, the
"/25" indicates the first 25 bits are used to identify the unique
network leaving the remaining bits to identify the specific host.
However, this scheme also cannot meet the demands put on address
allocation scheme put up by exponential growth of the Internet. In the
long run, CIDR will also suffer from address exhaustion problems.
Network Address
Translation(NAT)
This is another quick fix tried to solve the problems of IPv4 and
therefore, lacks any standardizations from the beginning. This mechanism
enables a local-area network (LAN) to use one set of IP addresses for
internal traffic and a second set of addresses for external traffic. A
NAT box located where the LAN meets the Internet makes all necessary IP
address translations. Hence, addresses allocated are locally unique but
not globally unique.
Connection Management in NAT
As stated previously, two different domains can share internal
IP addresses allocated to different hosts in the network. For instance,
a given Class A address can be used by two differnt domains say D1 and
D2. Each domain connects to the internet through one or more NAT boxes
(in case of multiple NAT boxes in a domain, each have indentical
translation tables).
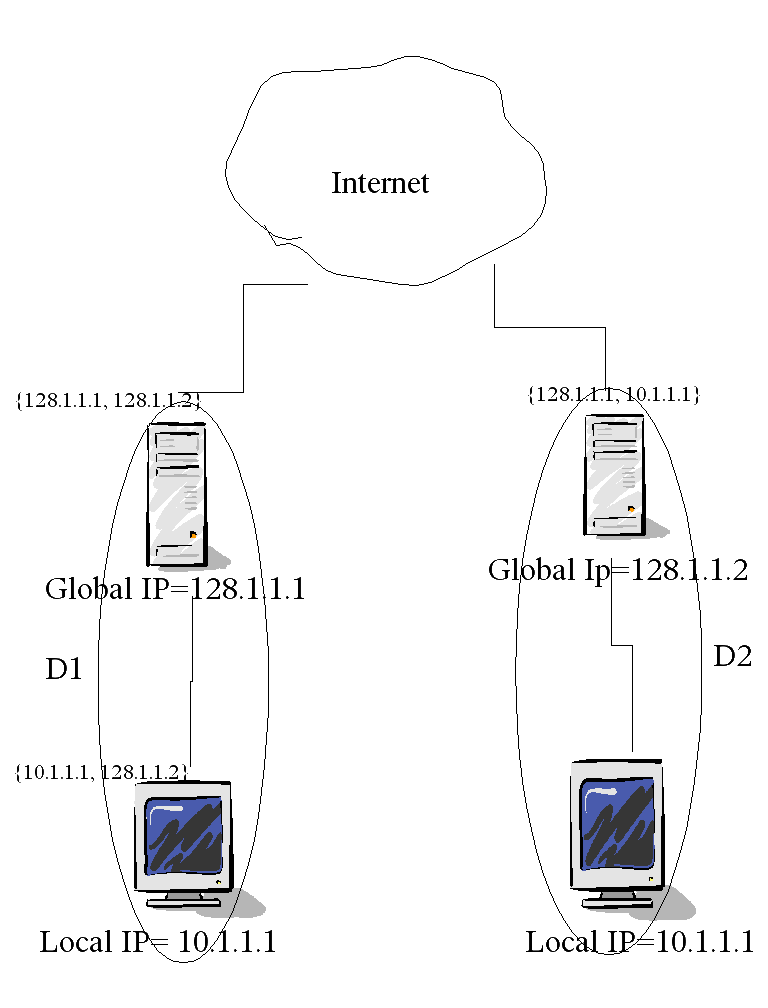
In above, each of D1 and D2 are using a particular Class A
address marked 10.0.0.0. A domain's NAT box is assigned a globally
unique IP address which in our example happens to be a class
C address 128.1.1.1 for D1 and 128.1.1.2 for D2. When D1's host 10.1.1.1
wishes to send a packet to D2's host 10.1.1.1, it uses the globally
unique address 128.1.1.2 as destination, and sends the packet to it's
primary router. The primary router has a static route for net D2's NAT
box, so the packet is forwarded on to the Internet after translating the
source address 10.1.1.1 of the IP header with its globally unique IP
address as shown in the figure. If there are multiple hosts behind a NAT
box with same IP address then ambiguity is resolved based on port
number. Clearly, this method requires no changes to hosts or
routers and address translation is totally transparent to them.
Advantages of NAT
Nat provides two important advantages which are:
- Address space reuse and hence extension as explained above.
- Site Isolation: A site behind a NAT can change its service
provider without having to change the IP addresses assigned to various
hosts on the site. Besides, service providers are also benefitted as
they now can renumber their networks in a way so as to attain address
aggregation.
- Multiple ISPs attachment to same customer: This is a consequence
of the site isolation that a site behind NAT can be attached to multiple
ISPs without appearing on free BGP enteries.
Disadvantages of NAT
- As is clear from the connection management explained above, NAT
breaks end-to-end semantics.
- Certain kinds of peer-to-peer applications are not possible
through NAT. This happens firstly, because there are no globally visible
addresses. And secondly, some applications cannot work due to address
translations and port translations done in NAT.
Two approaches to solve
IPv4 Address Exhaustion Problem
NAT Extended Architecture or IP Next Layer(IPNL)
IPNL preserves the following original features of IPv4
- globally visible long-lived address assignment to hosts
- statelessness of routers
- independence of network id from location
- good resistance to hijacking of packets
Of the above, the first two are more important. Other, major attributes
of IPNL are as follows:
- Its an extension, which implies that a maximum reuse of IPv4
infrastructure is made. This is accomplished by introduction of a new
layer between IP layer and the TCP layer which is called IPNL.
- In this scheme, changes only need to be done to the end-hosts and
the NAT boxes. The basic backbone remains intact i.e. no changes to DNS
or routers is require.
Architecture and Working of IPNL
We begin with the following definiions.
Private Realm ~ privately
addressed networks
Middle Realm ~ globally addressed
part of Internet.
NL-Routers ~Nat boxes
Frontdoor NL-Routers or FrontDoor: an
nl-router connecting a private realm to the middle realm
Internal NL-Router: an nl-router connecting
two private realms
Routing in IPNL can be done using FQDN(Fully Qualified Domain Name) or
IPNL addresses only. NL-routers can route packets using either kind of
address. A FQDN serves as a long-term address. Although a host can have
multiple FQDN addresses and these can be changed, however, an FQDN
address must not be changed during the lifetime of a single connection.
A disadvantage of using FQDN addresses is that they are of variable
length and routing using these is very inefficient. However, the
advantage is that no changes are required to IP address.
As with FQDN address, a host can have multiple IPNL addresses as well.
However, unlike the former these can be changed during the lifetime of a
single connection. FQDN addresses are required only during initial
connection establishment phase. Once the connection gets established,
subsequent packets can be routed using only the more flexible IPNL
addresses. The advantage with IPNL addresses is that they being short
and of fixed lenght, make routing efficient.
Routing by FQDN
To make FQDNs routable addresses, one or more DNS zones are associtated
with each realm. Conversely, every DNS zone is associated with exactly
one realm (although its parent zone may be spread over multiple realms).
The realm associated with a given DNS zone is called the home realm of
the zone. A zone can be attached to a realm other than its home realm,
in which case it is called, a visiting host and the realm to which it is
attached is called the visited realm. In the figure below, the home
realm for a.com is realm R1. Host y.a.com is a visiting host at realm
R6.
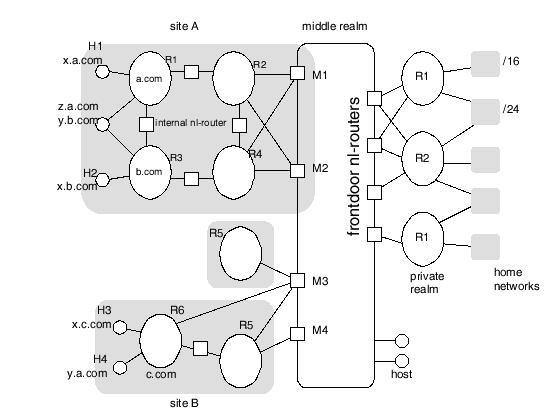
Example
IPNL Configuration
An internal nl-router that uses a frontdoor to connect to the middle
realm is said to be behind that
frontdoor. Dynamic maintainence of routing information is done to ensure
intra-zonal packet routing among various zones of the same frontdoor.
This routing information consists of the usual things: an explicit
forwarding table entry for the zone or a default entry towards the
frontdoor. Typically, an nl-router would contain explicit routing table
entries for zones in the same administrative domain, and a default entry
would be used for all other zones. At a minimum, though, the frontdoor
must have explicit routing table entries for all zones behind it.
Dynamic routing algorithms are used to acquire zone routing information.
Zones are treated as maskable addresses in the same way that IP
addresses are maskable. Whereas IP addresses are bit-maskable,
zones are maskable only at the "dot" boundaries. Hence, zone addressed
can be aggregated, however, not to the extent as IP addresses, because
of the following reasons:
- the assignment of domain names is primarily based on
administrative closeness, not topological closeness,
- there are lots of administrative domains
Because, in practice, an nl-router keeps explicit enteries
for only a fraction of which consist of those that lie behind the same
frontdoor, therefore, non-aggregatability of zone addresses is not a big
problem. In case, the destination zone is not behind the same frontdoor
as that of the source zone, then by default the packets are routed from
the source zone to the destination zone and then the conventional method
of routing through DNS lookups is followed. A third routing possibility
is routing a packet through an internal nl-router between hosts attached
to the same realm. For this, we require that internal nl-routers
maintain the following per-host routing information:
- The FQDN and private realm IP address of all hosts in
the realm, whether the host is visiting or not
- for each host whose home realm is the attached realm, but which
is visiting another realm, the FQDN of a zone in the visited realm must
be known.
An internal nl-router can learn of non-visiting hosts via a
DNS zone transfer. Visiting hosts must register both with an nl-router
in its home realm, and with an nl-router in its visited realm. When an
nl-router receives such a registration, it, in turn, informs all other
nlrouters attached to the realm. These neighbor nl-routers are learned
through static configuration. Because nl-routers must know about every
host in its attached realms as well as about every other attached
nl-router, it should be clear that private realms are not expected to be
very big. They should have only a fraction of the over 16 million
(figure below gives the IPNL address format, including the sizes of
various fields) possible hosts from the private address space. To
summarize, take the case where host x.a.com in figure above is sending a
packet to host x.c.com. Default routing gets the packet to frontdoor M1
(or M2). DNS information gets the packet from M1 to M4 (or M3). Dynamic
routing on zones gets the packet from M4 to the R5-R6 internal
nl-router. Internal nl-router R5-R6's host database gets
the packet from there to host x.c.com.
IPNL Based Routing
IPNL addresses has the structure as shown below:
- 4-byte globally unique IP address which is the middle realm IP
address(MRIP)
- 2-byte realm number(RN) to identify the realm behind the frontdoor
- 4-byte address of the end host within the realm specified above
by RN called the end host IP(EHIP) address
Iinternal nl-routers also know how to
route to each realm using the 2-byte RN. This routing information is
conveyed by the same dynamic routing protocol used for zones. This
protocol is very much similar to BGP. The AS numbers and IP prefixes of
BGP are analogous to RNs and zones respectively. That is in IPNL routes
to RNs are calculated and zones are associated with those. Packets for
realms behind different frontdoors are routed by default to the
frontdoor. Frontdoors use the MRIP to forward packets across the middle
realm. Once a packet reaches its destination private realm, the attached
nl-router uses the EHIP to forward the packet across the private realm
to the destination host. Note that the realm-routing protocol may
establish different forward and reverse paths between a host and its
frontdoor. Thus, we do not require any routing path symmetry assumptions
( of course, assumption is that the destination uses the MRIP specified
in the source address as part of the destination IPNL address for
packets in the reverse direction.)
Now, we repeat the example of a packet from host x.a.com to x.c.com,
but using IPNL addresses instead. The destination address for the packet
would be M4:R6:H3 (where M4 is the MRIP, R6 is the realm number, and H1
is the EHIP). Default routing gets the packet to M1(or M2). MRIP M4 gets
the packet from M1 to M4. Dynamic routing on RNs gets the packet from M4
to the R5-R6 internal nl-router. Internal nl-router R5-R6 uses the EHIP
H3 to deliver the packet to host x.c.com.
IPv6
Advantages for 128-bit Address Space
- Global reachability:
- no hidden nodes
- end to end security can be used
- every host can be a server
- Flexiblity: address space can have mutliple level of
hierarchy
- Autoconfiguration: use of 64 bits of MAC address will
ensure uniqueness and enable autoconfiguration abilities.
References:
- Paul Francis and Ramakrishna Gummadi, "IPNL: A NAT-Extended
Internet Architecture", ACM SIGCOMM, Aug 2001.
- Overview
of NAT on Zvon's RFC repository
- Florent
Parent, "IPv6 Tutorial", RIPE 40 Meeting, Prague, Czech Republic, Oct
2001.

