The Internet Protocol address is a 32- bit integer. If somebody wants to send a message it is necessary to include the destination address, but people prefer to assign machines pronounceable, easily remembered names (host names). For this reason the Domain Name System is used. These logical names also allow independence from knowing the physical location of a host. A host may be moved to a different network, while the users continue to use the same logical name.
The Domain Name System (DNS) is a distributed database used by TCP/IP applications to map between hostnames and IP addresses, and to provide electronic mail routing information. Each site (university department, campus, company, or department within a company, for example) maintains its own database of information and runs a server program that other systems across the Internet can query. The DNS provides the protocol which allows clients and servers to communicate with each other.
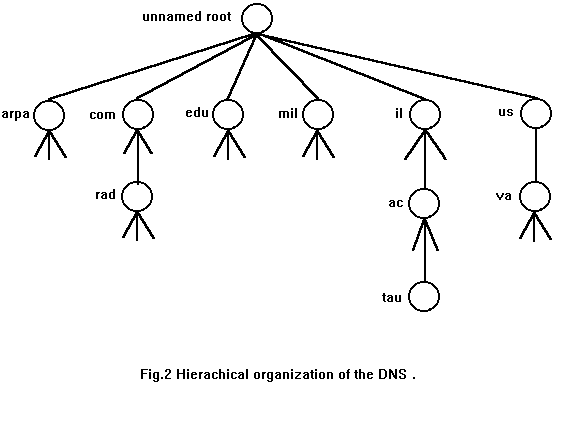
The system accesses the DNS through a revolver. The revolver gets the hostname and returns the IP address or gets an IP address (fig.1) and looks up a hostname. As we can see in fig.1 the revolver returns the IP address before asking the TCP to open a connection or sending a datagram using UDP.
DNS design goals
- The primary goal is a consistent name space which will be used for
referring to resources. Names should not be required to contain network
identifiers, addresses, routes, or similar information as part of the name.
- Name space should be maintained in a distributed manner, with local caching to
improve performance. Mechanisms for creating and deleting names; these should
also be distributed.
- The costs of implementing such a facility dictate that it be generally useful,
and not restricted to a single application. We should be able to use names
to retrieve host addresses, mailbox data, and other as yet undetermined
information. All data associated with a name is tagged with a type, and queries
can be limited to a single type.
- The name space should be useful in dissimilar networks and applications.
Design Principles
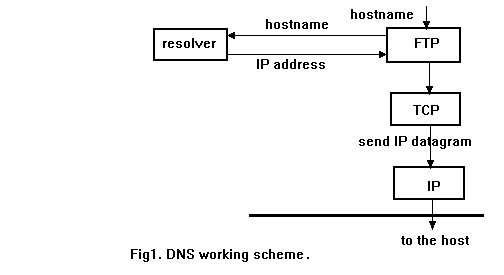
Hierarchy: The domain name system uses a hierarchical naming scheme known as domain names, which is similar to the Unix file system tree. The root of the DNS tree is a special node with a null label. The name of each node (except root) has to be up to 63 characters. The domain name of any node in the tree is the list of labels, starting at that node, working up to the root, using a period ("dot") to separate the labels (individual sections of a name might represent sites or a group, but the domain system simply calls each section a label ). Thus, the domain name "tau.ac.il" contains three labels: "tau", "ac", and "il". Any suffix of a label in a domain name is also called a domain. In the above example the lowest level domain is "tau.ac.il" (the domain name for the Tel-Aviv University Academic organization in Israel), the second level domain is "ac.il" (the domain name for Academic organizations of Israel), and the top level domain (for this name) is "il" (the domain name for Israel). The node il is the second level node (after root) (Fig.2)

Caching : A fundamental property of the DNS is caching. That is, when a name server receives information about a mapping, it caches that information. Thus a later query for the same mapping can use the cached result. The DNS uses the caching for optimizing search cost.
Every server has a cache for recently used names as well as a record of where the mapping information for that name was obtained. When a client asks the server to resolve certain name the server does as follows:
1.Check if it has authority for the name. If yes, the server doesn't need caching information.
2.If not, the server checks its cache whether the name has been resolved recently. if yes, the server reports the caching information to its clients.
We can examine the cache when the server cashed the information once, but didn't change it. Since information about a particular name can change, the server may have incorrect information in its caching table. The Time to Live (TTL) value is used to decide when to age information. Whenever an authority responds to a request, it includes a TTL value in the response which specifies how long it guarantees the binding to remain.
Of the 3 components in the CAP principle ( consistency, Availability, resilience to partition) DNS opts for Availability and resilience to Partition.
DNS Architecture
NAME SERVERS are server programs which hold information about the domain tree's structure and set information. A name server may cache structure or set information about any part of the domain tree, but in general a particular name server has complete information about a subset of the domain space, and pointers to other name servers that can be used to lead to information from any part of the domain tree.
REVOLVERS are programs that extract information from name servers in response to client requests. Revolvers must be able to access at least one name server and use that name server's information to answer a query directly
Data in the DNS consists of Resource Records. There exists a data type for each record. It is of the form (A, MX) where A is the 32-bit IP address, MX is a 16-bit value along with a host name which acts as the mail exchange for the domain.
DNS Zones
The zone is a subtree of the DNS that is administered separately. Whenever a new system is installed in a zone, the DNS administrator for the zone allocates a name and an IP address for the new system and enters these into the name server's database. Within a zone DNS service for subsidiary zones may be delegated along with a subsidiary domain. A name server can support multiple zones.
Remarks on DNS
DNS for System break-in
DNS is highly vulnerable to attacks and spoofing. An intruder can intercept virtually all requests to translate names to IP addresses, and supply the address of a subverted machine instead; this would allow the intruder to spy on all traffic, and build a nice collection of passwords if desired.
IP spoofing attacks can be prevented to an extent. Ssh provides an improved type of authentication. The server has a list of host keys stored in /etc/ssh_known_host, and additionally each user has host keys in $HOME/.ssh/known_hosts. Ssh uses the name servers to obtain the canonical name of the client host, looks for its public key in its known host files, and requires the client to prove that it knows the private host key. This prevents IP and routing spoofing attacks.
rlogin and rsh permit ordinary users to extend trust to remote host/user combinations. In that case, individual users, rather than an entire system, may be targeted by source routing attacks. The information required for this attack are the target hostname, trusted hostname and the user name, which are obtained by the "finger" command.
Attack is done as below:
In spoofing a host or application to mimic the actions of another. The attacker pretends to be an innocent host by following IP addresses in network packets. rlogin service can use this method to mimic a TCP connection from another host by guessing TCP sequence numbers.
These attacks can be prevented by :
Allowing to do forward lookup creates a problem called " poisoning the cache " where the attacker sends an unsolicited record along with the PTR record( PTR-a pointer to another part of the domain name space ).
This attack can be subverted by rejecting with the record which arrives along with the PTR record.