ASYMMETRIC
NETWORKS
Asymmetry in Networks (in terms of forward Ė backward direction) can be of many types such as bandwidth, latency and packet error rates. This kind of asymmetry is more evident in wireless networks.
Bandwidth Asymmetry: The bandwidth in the forward direction (from a server/router to a host) is usually higher when compared to the backward direction (a host to a server/router). The Bandwidth asymmetry can actually result in other kinds of asymmetries. Due to this we can have different latencies in upstream (backward) and forward (downstream) directions.
Packet Error Rates: In a wireless net work there is higher packet error rate in the wireless part of the network when compared the wired part of the network.
Routing Asymmetry: This sort of asymmetry exists if upstream packets take a different route when compared to the downstream packets.
Since Asymmetric Bandwidth influences other network properties. It is important to consider this asymmetry in detail. We will also discuss some solutions to overcome this problem.
Bandwidth Asymmetry
Consider a network with the following Bandwidth and Packet size parameters
|
|
Forward |
Reverse |
|
Bandwidth |
100 Mbps |
100 Kbps |
|
Packet Size |
1000 bytes |
40 bytes |
So,
Bandwidth Ratio (b): 1000
Packet Size Ratio (p): 25
Dividing b by p we get Normalized Bandwidth ratio, b/p= 40, which means that we can send an ACK once for every 40 packets.
In other words, if the packets (bytes) in one direction (forward) are being sent at a faster rate than in the other direction (reverse), then the bandwidth utilization is poor in the forward direction, this is because of the Self Clocking nature of† TCP (a sender sends packets only on receiving ACK from the receiver). So Bandwidth Asymmetry can have the following implications:
1. poor bandwidth utilization in the forward direction ( or downstream)
2. loss of some of the ACK packets
3. TCP clocking mechanism can breakdown
Asymmetric Network Solutions
- ACK Congestion Control: In this solution the TCP receiver detects the loss of the ACK packets and it send the ACKs at a slower rate, thereby compensating for the asymmetry in the network. The bottleneck router will have to make use some mechanism such as RED (Random Early Detect) to detect the ACK packet loss and notify the TCP receiver about this. By this the receiver will slow down the rate at which it is sending the ACKs
- ACK Filtering: The bottleneck routers will filter out the earlier or the ďstaleĒ ACKs in its buffer. Thus the bottleneck router tries to send only the latest ACK when there is a backlog of ACKs in its buffer. The bottleneck router doesnít have to maintain per flow state information, it only has to compare the latest ACK with the ones in the buffer which are yet to be routed.
- Sender Adaptation: This is different from the previous solutions in the sense that it is the sender which makes an active effort to tackle the asymmetric network. The sender keeps track of the number of segments that have been acknowledged rather than the number of ACKs that have been received. Using this information it calculates the sending rate which is
Sending rate = cwn
/ rtt
††††††††††††††††††††††††††††††††††††††††††††††† Where
††††††††††††††††††††††††††††††††††††††††††††††††††††††††††† cwn= congestion window size
††††††††††††††††††††††††††††††††††††††††††††††††††††††††††† rtt=††† round trip delay
††††††††††† It then regulates the sending rate according to the number of segments that have been acknowledged.
- Routers can prioritize the ACKs.
MOBILE
IP
Introduction
In the present day Internet, the identity of a host and the physical location of the machine are intertwined (or tightly coupled). Mobile IP tries to decouple this Identity-Location pair by providing a level of Indirection. There are many other instances in which we see this level of indirection i.e. situations in which identity is independent of the location.
E.g.††††† File System: The filename is independent of itís location on a Fileserver
Mobile Phones: The phone # is independent of the current location of the user (it is the same wherever the user may be)
Definitions
The following terminologies are relevant in the Mobile IP Architecture:
Mobile Host: A host that may connect to the Internet in the networks other than its own home network, while still using its home address.
Correspondent Host: A host communicating with another host. This term is used when it is not relevant whether this host is mobile or a stationary host.
Home Address: An address used to identify a mobile host, no matter where it may currently be located.
Home Network: The (logical) network on which a mobile hostís home address resides.†
Care-of Address: An address that defines the location of the mobile host at some particular instant of time. Packets addressed to the mobile host will arrive at this address.
Foreign agent: An agent that offers a care-of address for visiting mobile hosts, and delivers arriving packets addressed tone of these mobile hosts locally to the mobile host.
Home agent: An agent that maintains information about the current care-of address of each of the mobile hosts it configured to serve, and that forwards packets (addressed to any of these mobile hosts) to the care-of address for that mobile host.
Triangle routing: A situation in which a correspondent hostís packets to a mobile host are forwarded through the mobile hostís home agent, rather than following the shortest path directly to the mobile host.
Basic Operation
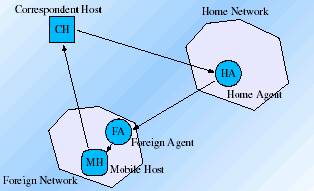
An inherent feature of a mobile host is that it may move anywhere throughout the IP internetwork. It is assigned a constant IP address on a home network, known as its home address. Correspondent hosts may always use the home address to address to address packets to a mobile host.
A mobile host has a home agent, which it is attached to its home network. Each home agent maintains a list of mobile hosts that it is configured to serve along with their respective current locations. This list is known as home list.
When a mobile host connects to the network, it must perform a registration process before packets will be delivered to it. Each foreign agent maintains a list known as visitor list, which identifies those mobile hosts that are currently registered with it. The address of the foreign agent, supplied as the mobile hostís care-of address, defines the mobile hostís current location. The combination of a home address and a care-of address is known as a binding. The registration protocol ensures that a mobile hostís home agent learns about the new binding of any mobile host it serves. The registration protocol also notifies the previous foreign agent(s) that the mobile host has moved.
Any node may cache the current binding of a mobile host in order to be able to forward packets directly to that mobile host. A mobile hostís previous foreign agent may cache the new binding of the mobile host form the notification sent during the new registration; this cache entry serves as the a ďforwarding pointerĒ to allow packets to be forwarded to its new location.
The Mobile IP must direct the packets destined to a mobile host to its current known location (care-of address). Tunneling technique is employed to send packets to a mobile hostís current location. Tunneling involves the use of an encapsulation protocol which involves encapsulation of the data packet to reach the tunnel endpoint, and decapsulation when the packet is delivered at that endpoint. The default tunnel mode is IP Encapsulation within IP Encapsulation.
REFRENCES
http://www.cse.iitk.ac.in/users/braman/courses/cs625-fall2004/lec-slides/lec16.sxi.pdf
http://www.cse.iitk.ac.in/users/braman/courses/cs625-fall2004/lec-notes/lec-notes16-1.html
[MPJ94]
Andrew Myles, Charles Perkins, and David B. Johnson, "The Internet