Lecture No. 27
Date :- 22 Oct. 2003
Scribe by :- Preeti Goel(Y3111032)
Domain Name System (DNS)
Using DNS for System Break-ins
DNS(Domain Name System)
Domain Name System maps a name to an IP address and conversely an address to a name.
Initially when the size of the Internet was small all machines used to maintain a host.txt file which was passed on incase of Updates.This host.txt file was centrally managed but looking at the present Internet scenario this does not seem to be a feasible option due to the following reasons:
Size of the file will be very large, scalability also becomes an issue
This is centrally managed but since the internet has distributed management, the management of name space should also be of distributed nature.
There can be inconsistent results for queries.
Because of the centralized management as the frequency of lookups increases the time for reply can be very large.
DNS Design Goals
1) Distributed ownership: Since the internet has distributed ownership, the ownership of name space should also be of distributed nature.
2)Have no obvious size limits for names, name components, data associated with a name, etc.
3)DNS protocol should be independent of the network topology.
4)OS/Architecture independent (Case independent)
Design Principles
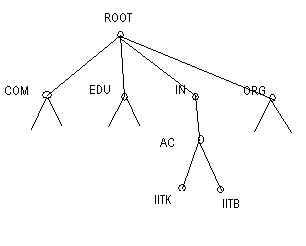
HIERARCHY :The name space as well as management space should be hierarchical. The name space can be represented as a tree with the root label as a null string.

Each node in the tree defines a domain which is an index to the domain name space database. Management is representative of name space.
CACHING: Caching is required as otherwise there will be
long time for lookup
congestion at the root server
It is implemented using the TTL,which is specified at the time of configuration.eg:A TTL value of zero implies no caching generally used for web mirrors.
TTL value imposes a tradeoff between consistency achieved for low TTL) verses Update frequency low for high values of TTL)
It is a digression, (Consistency, Availability, resilience to Partition) CAP .CAP principle says that only two of the three can be implemented at a time.
Example :If consistency and resilience to partition are implemented then a copy cannot be updated across a partition. Locks are to be implemented for consistency which reduces the availability.
DNS chooses Availability and redilience to Partition and sacrifices Consistency.
CAP has 2 versions
Strong CAP: Pick any 2 components of the 3.
Weak CAP: It is relative as in if one component is increased some other has to go down. Example CODA (wireless file system )
LEVEL OF INDIRECTION: DNS introduces a level of indirection which can have several uses. Example :to match to the closest mirror site.
DNS Architecture
The active components of the DNS are of two major types: name servers and resolvers. Name servers are repositories of information, and answer queries using whatever information they possess. Resolvers send out queries for a particular mapping, and embody the algorithms necessary to find a name server that has the required information.
Data for each name in the DNS is organised as a set of Resourse Records(RR).Each RR has an associated type and class.Example (A,MX) where A is the address and MX is mail server.
DNS can be used for both forward lookup (host name to IP address ) and reverse lookup( IP address to host name). Name space has an entire subtree for reverse mapping.e.g. INADDR.ARPA for reverse lookup
DNS Zones
Zones are contigous regions of the name space, where each can be forked into subzones.Each of this subzone can have its independent management.
Eg: The IITK zone has 2 sub zones cse and lib which have their own managenment.
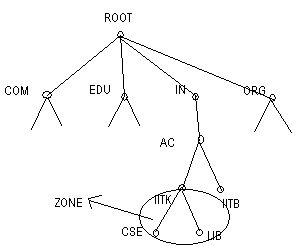
A name server can support multiple zones, several sub zones can use the same name server. Name servers have pointers among each other.
REMARKS ON DNS
DNS uses datagram based access, although a DNS query requires reliability, TCP is not used as it is a query response mechanism.
Root server is replicated for improved reliability.
Additional information is given considering the future needs of an application. Eg. both reverse and forward lookup info can be returned.
System Break-In
The central problem in DNS is that it has no authentication mechanism. IP spoofing is an easy attack for internet as no source checking is done ,but IP spoofing attacks are difficult here (as preferably the attacker has to be on the path between the victim and the attacker).
Attack to rlogin/rsh where a list of trusted host names is specified for a local machine in ~./rhosts file can be done as
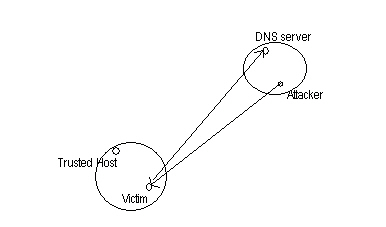
Attacker connects to victim using a trusted host's name.
The victim does a reverse lookup, on the DNS server in the attackers domain
If the attacker has control over the DNS server in its domain or can send spurious reply associating the attackers IP address with the trusted host's name then a system break in has been done successfully.
The information required for this attack is the victims host name, attacker's host name and the user name. This information can be easily acquired using the finger daemon or SNMP queries etc.
DNS can be made secure by
Maintaining list of secure IP addresses instead of host names.
Follow up the reverse mapping of the IP address with a forward mapping and compare the addresses, which if different indicate an attack.
However ,if additional information is supplied along with the reverse query (in the form of forward mapping) by the attacker then this countermeasure fails. This is known as "Poisoning the Cache". Solution for this can be
i)additional information supplied along with the reverse lookup can be rejected.
ii)Make the victim do a valid DNS query apart from the lookup. eg.email with a query
3. Application can do crypto authentication instead of depending on DNS.eg KERBEROS
Hence DNS authentication is required which can be implemented by applications themselves or by maintaining logs.