CS625 – Advanced Computer Network
Instructor – Bhaskaran Raman
Lecture 16 ( Sep 09, 2003)
Scribe – Rajiv Kumar Ranjan (Y3111037)
Asymmetric
networks
The common asymmetries exist
in a network due to :
Bandwidth:
New network technologies provide much larger downstream
bandwidth (towards the user) than upstream bandwidth (away from the
user). The asymmetry in bandwidth could range from a factor of 10 to
1,000.
Latency:
In certain wireless networks, the underlying media access
control (MAC) protocol often results in a significantly larger one-way
latency from a base station to a mobile station than in the reverse
direction. In other networks there is a significant delay when a node
switches from sending to receiving mode or vice versa.
Packet errors:
The incidence of packet errors could be much greater in the upstream
direction than in the downstream direction. This could be inherent in
the network technology or the result of distinct upstream and downstream
technologies .
These asymmetries
could have an adverse effect on TCP performance due to several reasons:
the limited upstream bandwidth could throttle the flow of TCP
acknowledgment packets and disrupt TCP's ack clocking mechanism, the
asymmetry in latency could cause large variations in TCP's roundtrip
time estimate, etc.
We will concentrate mainly over the asymmetry caused by
band-width, because it is much common than other ones.
Band-width Asymmetry:
Asymmetric links are characterised by having different
bandwidths for each direction of the communication. There are many TCP
applications such as Web access or FTP in the Internet that take
advantage of this fact, because they involve a substantially larger flow
of data in the forward direction (from host to client) than in the
reverse direction ( from client to host). These applications are based
on the TCP.
TCP performance can suffer an important degradation when data is
transmitted through asymmetric links.When a connection is established,
packets are sent through the forward channel and acks through the
reverse channel. If it is generated one ack for each received packet,
acks are generated faster than the link rate.As the TCP behaviour is
self-clocking, property according to which the transmission of packets
at the sender is made after the reception of acks, the forward data
transfer can be slow down.
Thus, asymmetry in
band-width might cause
-
Ack congestion : Here Acks get
spaced out. Congestion can be controlled by allowing only one Ack for
k data packets received, where k is the normalized bandwidth ratio.
-
Ack loss : Ack loss might result in sender to be slowed down.
Also, the behaviour of sender may be bursty.
-
Data throughput in forward direction to be limited: It happens
due to bandwidth-constrained reverse channel.
( Normalised bandwidth ratio:
The Normalised bandwidth ratio, k, between the forward anfd reverse
paths is the ratio of the raw bandwidth divided by the packet sizes used
in the two directions.
If forward channel bandwidth = 10Mbps , Packet size = 1000 bytes,
reverse channel bandwidth = 10Kbps and ack size = 40
bytes,
then, normalised bandwidth ratio = (10Mbps/1000B)/(10Kbps/40B)= 40. )
Solutions:
The possible solutions are:
Ack congestion control :
This is basically an end-to-end solution done at the receiver. If TCP
receiver can learn of Ack loss, then it can send Acks at a slower rate.
For this, the mechanism employs a dynamically varying delayed-ack
factor ( this factor represents the no. of packets received for which
single ack is sent ) based on the congestion of acks in the reverse
link. Although this mechanism is effective to control the congestion of
the reverse link, its effectineness reduces in the presence of packet
losses due to errors.
Ack filtering mechanism:
It is based on controlling the amount of acks enqueued at the reverse
link router. When a new ack is received, some fraction of the acks (
possibly all but one) belonging to the same connection is
removed.Therefore, the frequency of the acks preventing the slow down
of the forward data transfer.Its effectiveness against congestion or
losses, because it acts directly where it takes place. Here no per-flow
state is required in router.
- Sender Adaption:
In this approach, the sender sends according to the number of segments
acknowledged and not based on the number of Acks. i.e. the window
growth is tied to amount of data acked rather than the number of acks
received. So, potentially large bursts are broken up into smaller ones.
- Acks-first Scheduling:
Router can schedule Acks with priority. Here, again, no
per-flow state is required.
- Mobile
IP
Mobile IP is an open standard,
defined by the Internet Engineering Task Force (IETF) RFC 2002, that
allows users to keep the same IP address, stay connected, and
maintain ongoing applications while roaming between IP networks. Mobile
IP is scalable for the Internet because it is based on IP -- any media
that can support IP can support Mobile IP.
Before discussing the various issues of mobile IP, we first
address the mobility problem.
The Mobility Problem:
"If a host moves only locally, there may be no problem if the
local subnet is flat addressed. But, Longer distance moves require
global routing updates, which is obviously impractical in a large
network even for small no. of moving hosts."
Although Hierarchical, topologically- based addressing ( in which
at least part of the address identifies approximate location ) is fine
for scaling a network consisting of nodes whose network attachment
points don't change, it is not suitable for nodes which are movable ones
(i.e. Mobile nodes). The reason is that the routers only need to know
the way to each network, but if a host moves, its packets will still go
to its home!
The above problem arises due to the fact that Internet routing is titghtly coupled with
addressing and the usual addressing couples the identity and
location of the nodes. So, we need a way to seperate identity from location.
For this, we introduce a level of
indirection on the addressing scheme, which forms the basis of the
Mobile IP.
Mobile IP works in the following way:
-
Leave the hierarchical network
intact
-
Craete special entities that "own"
the mobile host address
-
Mobile hosts report their
locations (register) with the stationary entities
-
Traffic to the mobile Hosts is
relayed by the stationary entities.
Requirements:
-
Compatibility - work with exiting
computers communicating with TCP, HTTP, work with existing operating
systems , should not affect all routers ( some is ok, but not all ).
-
Transparency - mobility should
remain invisible to higher layer , mobile clients may notice
interruptions or lower bandwidth, but basically everything should
still work during movement , senders of messages should not be aware
of client mobility.
-
Scalability and efficiency - do
not reduce the efficiency of network.
-
Security - Authentication of all
messages related to management , If a packet is sent to a mobile
host, that mobile host should be the one to receive it.
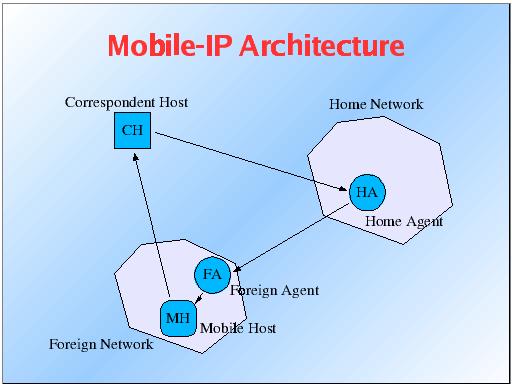
The Basic Architecture:
Each mobile host (MH) has a home agent (HA) that acts as a
location registry, maintaining the binding from the MH's home address
and its foreign care-of-address. Each time the MH moves, this
binding is updated. Correspondent hosts (CH's) address messages with the
MH's home address; the HA forwards this message to the MH via IP
tunneling or encapsulation. MH's gain their care-of-addresses by
contacting a foreign agent; the foreign agent assigns the
care-of-address and updates the MH's binding by contacting the HA. This
updation requires some authentication informations. The whole pocess is
explained below.
The Mobile Host is a device such as a personal
digital assistant, or laptop whose software enables network roaming
capabilities.
The Home Agent is a router on the home network
serving as the anchor point for communication with the Mobile host; it
tunnels packets from a device on the Internet, called a Correspondent
Host, to the roaming Mobile Host. (A tunnel is established between the
Home Agent and a reachable point for the Mobile Host in the foreign
network.)
The Foreign Agent is a router that may function as
the point of attachment for the Mobile Host when it roams to a foreign
network, delivering packets from the Home Agent to the Mobile Host.
The care-of address is the termination point of the
tunnel toward the Mobile Host when it is on a foreign network. The Home
Agent maintains an association between the home IP address of the Mobile
Host and its care-of address, which is the current location of the
Mobile Host on the foreign or visited netwok.
The basic Architecture of Mobile-IP is
shown below:
Working
of Mobile IP:
The Mobile IP process
has three main phases, which are discussed below:
Agent Discovery:
A Mobile Host discovers its Foreign and Home Agents during agent
discovery. During the agent discovery phase, the Home Agent and
Foreign Agent advertise their services on the network. The Mobile Host
listens to these advertisements to determine if it is connected to its
home network or foreign network. If a Mobile Host determines that it is
connected to a foreign network, it acquires a care-of address which is
provided by the foreign agent. When the Mobile Host hears a Foreign
Agent advertisement and detects that it has moved outside of its home
network, it begins registration.
Registration:
Th e Mobile Host sends the registration request to its
Home Agent. The Home Agent checks the validity of the registration
request, which includes the care-of-address and authentication of the
Mobile Host. If the registration request is valid, the Home Agent
creates a mobility binding (an association of the Mobile Host with its
care-of address), a tunnel to the care-of address, and a routing entry
for forwarding packets through the tunnel.
Thus, a successful Mobile IP registration sets up the routing mechanism
for transporting packets to and from the Mobile Host as it roams.
Tunneling:
The Mobile Host sends packets using its home IP address, effectively
maintaining the appearance that it is always on its home network. Even
while the Mobile Host is roaming on foreign networks, its movements are
transparent to correspondent Hosts. Data packets addressed to the
Mobile Host are routed to its home network, where the Home Agent now
intercepts and tunnels them to the care-of address toward the Mobile
Host. Tunneling has two primary functions: encapsulation of the data
packet to reach the tunnel endpoint, and decapsulation when the packet
is delivered at that endpoint. The default tunnel mode is IP
Encapsulation within IP Encapsulation.
Finally, the Mobile Host sends packets directly to their final
destination, i.e. the Correspondent Host.
The following figure summarises the above process:
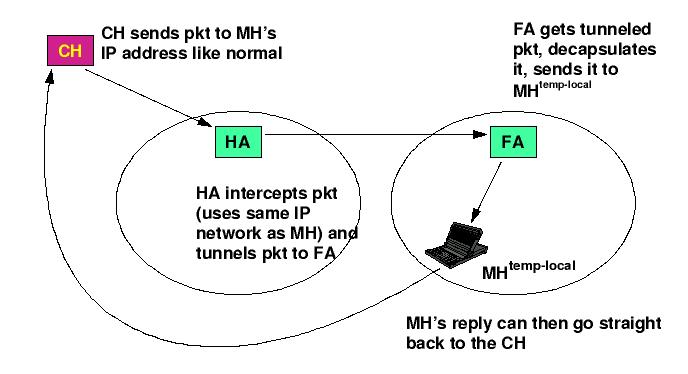
MH: Mobile Host
CH: Correspondent Host
HA: Home Agent
FA: Foreign Agent
--------------------------------------------

